The Wireless Revolution
The Wireless Revolution
Devices that support wireless or mobile communication and computing include:
- Cell phones
- Personal digital assistants (PDAs): Small, handheld computers featuring applications such as electronic schedulers and address books
- E-mail handhelds: A special type of handheld that is optimized for wireless text messaging
- Smart phones: Hybrid devices combining the functionality of a PDA with that of a digital cell phone
Digital cellular service uses several competing standards that are incompatible.
- Global System for Mobile Communication (GSM) is the standard used in Europe and much of the rest of the world outside the United States. GSM's strength is in international roaming capabilities.
- Code Division Multiple Access (CDMA) is the most widely used standard in the United States. CDMA is less expensive and supports higher quality transmissions.
Most digital cellular systems today can transmit data at rates ranging from 9.6 to 2 Mbs. 384 Kbps is acceptable for email but not for downloading large files or Web pages.
Short message service (SMS) is a text message service used by a number of digital cell phone systems to send and receive short alphanumeric messages.
2.5G networks use upgrades to the existing cellular infrastructure and feature data transmission rates ranging from 30 to 144 Kbps.
More powerful cellular networks called third-generation (3G) networks have transmission speeds ranging from 384 Kbps for mobile users in, say, a car, to more than 2 Mbps for stationary users, sufficient for rich media downloads.
5G is the 5th generation mobile network. It is a new global wireless standard after 1G, 2G, 3G, and 4G networks. 5G enables a new kind of network that is designed to connect virtually everyone and everything together including machines, objects, and devices.
There are also multiple standards and technologies governing how cellular phones access the Internet and the World Wide Web.
Short message service (SMS) is a text message service used by a number of digital cell phone systems to send and receive short alphanumeric messages.
2.5G networks use upgrades to the existing cellular infrastructure and feature data transmission rates ranging from 30 to 144 Kbps.
More powerful cellular networks called third-generation (3G) networks have transmission speeds ranging from 384 Kbps for mobile users in, say, a car, to more than 2 Mbps for stationary users, sufficient for rich media downloads.
5G is the 5th generation mobile network. It is a new global wireless standard after 1G, 2G, 3G, and 4G networks. 5G enables a new kind of network that is designed to connect virtually everyone and everything together including machines, objects, and devices.
There are also multiple standards and technologies governing how cellular phones access the Internet and the World Wide Web.
- Wireless Application Protocol (WAP) is a system of protocols and technologies that enables cell phones and other wireless devices with tiny display screens, low-bandwidth connections, and minimal memory to access Web services.
- A microbrowser is an Internet browser that works with the low-memory constraints and low bandwidth requirements of handheld wireless devices and uses WML (Wireless Markup Language). Requests are made to a WAP gateway which translates HTML content into WML for the WAP client to receive it.
- I-mode is a wireless service offered by Japan's NTT DoCoMo mobile phone network that uses compact HTML instead of WML for delivering content.
Figure 7-15
 |
FIGURE 7-15 WIRELESS APPLICATION PROTOCOL (WAP) VERSUS I-MODE WAP and I-mode use alternative standards for accessing information from the wireless Web. |
There is a hierarchy of complementary standards for wireless computer networks designed for connecting to personal area networks (PANs), LANs, MANs, and WANs.
Bluetooth, or IEEE 802.15, uses the 2.4-GHz band for creating small PANs, linking up to eight devices within a 10 meter area. devices can communicate to each other without direct user intervention. Its low power requirements make Bluetooth appropriate for battery-powered handhelds, cell phones, or PDAs.
Figure 7-16
Bluetooth, or IEEE 802.15, uses the 2.4-GHz band for creating small PANs, linking up to eight devices within a 10 meter area. devices can communicate to each other without direct user intervention. Its low power requirements make Bluetooth appropriate for battery-powered handhelds, cell phones, or PDAs.
Figure 7-16
 |
FIGURE 7-16 A BLUETOOTH NETWORK (PAN) Bluetooth enables a variety of devices, including cell phones, PDAs, wireless keyboards and mice, PCs, and printers, to interact wirelessly with each other within a small 30-foot (10-meter) area. In addition to the links shown, Bluetooth can be used to network similar devices to send data from one PC to another, for example. |
Wi-Fi (wireless fidelity), or IEEE 802.11 includes three standards:
- 802.11a: This standard can transmit up to 54 Mbps in the 5-GHz band, in ranges of 10-30 meters.
- 802.11b: This standard, currently the most popular, transmits up to 11 Mbps using the 2.4 GHz band with a range of 30-50 meters.
- 802.11g: This standard also uses the 2.4 GHz band and can transmit up to 54 Mbps.
Wi-Fi system can operate in two modes:
- Infrastructure mode, in which wireless devices communicate with a wired LAN through access points
- Ad-hoc mode, or peer-to-peer mode, in which the devices communicate directly to each other.
Figure 7-17
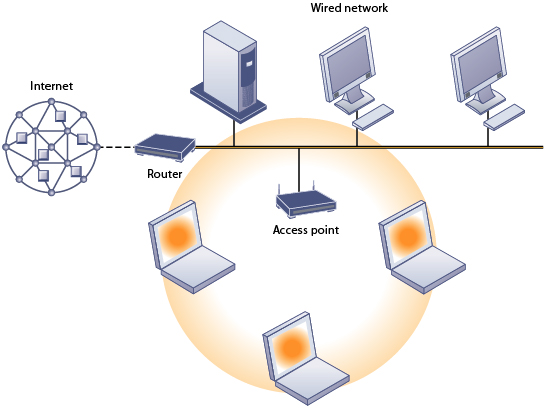 |
FIGURE 7-17 AN 802.11 WIRELESS LAN Mobile laptop computers equipped with network interface cards link to the wired LAN by communicating with the access point. The access point uses radio waves to transmit network signals from the wired network to the client adapters, which convert them into data that the mobile device can understand. The client adapter then transmits the data from the mobile device back to the access point, which forwards the data to the wired network. |
Mobile wireless stations often need a wireless network interface card (NIC) that has a built-in radio antenna.
The 802.11 standard can be used to provide wireless Internet access, in which an access point plugs into a wired Internet connection. Businesses are using Wi-Fi to create low costs WLANs and provide Internet access.
Hotspots are one or more access points positioned strategically in public spaces and provide wireless coverage for a specific area. Many free public hotspots are available in the US and other countries. However, users cannot roam from hotspot to hotspot if these use different Wi-Fi network services. Wi-Fi also has weak security features, and is susceptible to interference from nearby systems operating in the same spectrum, such as microwave ovens or wireless phones.
WiMax (Worldwide Interoperability for Microwave Access), or IEEE 802.16, is a new set of standards that has an access range of up to 31 miles and data transfer rates up to 75 Mbps, using WiMax antennas to beam high-speed Internet connections to rooftop antennas of homes and businesses.
Broadband Internet access can also be configured through cellular telephon e networks. Major cellular telephone carriers have configured their 3G networks to provide broadband access for PCs and other handheld devices. EV-DO (Evolution Data Optimized), used by Verizon, provides wireless Internet access over a cellular network at speeds form 300 to 500 Kbps.
Radio frequency identification (RFID) systems provide a powerful technology for tracking the movement of goods throughout the supply chain. RFID systems use tiny tags with embedded microchips containing data about an item and its location to transmit radio signals over a short distance to special RFID readers. The RFID readers then pass the data over a network to a computer for processing. Unlike bar codes, RFID tags do not need line-of-sight contact to be read.
The transponder, or RFID tag, uses a microchip to store information unique to the item, such as an electronic identification code, where and when it was made, or its status during production. The rest of the tag is an antenna that transmits data to the reader. The reader unit consists of an antenna and radio transmitter with a decoding capability attached to a stationary or handheld device. The reader emits radio waves in ranges anywhere from 1 inch to 100 feet, depending on its power output, the radio frequency employed, and surrounding environmental conditions. When a RFID tag comes within the range of the reader, the tag is activated and starts sending data. The reader captures these data, decodes them, and sends them back over a wired or wireless network to a host computer for further processing.
Figure 7-18
The 802.11 standard can be used to provide wireless Internet access, in which an access point plugs into a wired Internet connection. Businesses are using Wi-Fi to create low costs WLANs and provide Internet access.
Hotspots are one or more access points positioned strategically in public spaces and provide wireless coverage for a specific area. Many free public hotspots are available in the US and other countries. However, users cannot roam from hotspot to hotspot if these use different Wi-Fi network services. Wi-Fi also has weak security features, and is susceptible to interference from nearby systems operating in the same spectrum, such as microwave ovens or wireless phones.
WiMax (Worldwide Interoperability for Microwave Access), or IEEE 802.16, is a new set of standards that has an access range of up to 31 miles and data transfer rates up to 75 Mbps, using WiMax antennas to beam high-speed Internet connections to rooftop antennas of homes and businesses.
Broadband Internet access can also be configured through cellular telephon e networks. Major cellular telephone carriers have configured their 3G networks to provide broadband access for PCs and other handheld devices. EV-DO (Evolution Data Optimized), used by Verizon, provides wireless Internet access over a cellular network at speeds form 300 to 500 Kbps.
Radio frequency identification (RFID) systems provide a powerful technology for tracking the movement of goods throughout the supply chain. RFID systems use tiny tags with embedded microchips containing data about an item and its location to transmit radio signals over a short distance to special RFID readers. The RFID readers then pass the data over a network to a computer for processing. Unlike bar codes, RFID tags do not need line-of-sight contact to be read.
The transponder, or RFID tag, uses a microchip to store information unique to the item, such as an electronic identification code, where and when it was made, or its status during production. The rest of the tag is an antenna that transmits data to the reader. The reader unit consists of an antenna and radio transmitter with a decoding capability attached to a stationary or handheld device. The reader emits radio waves in ranges anywhere from 1 inch to 100 feet, depending on its power output, the radio frequency employed, and surrounding environmental conditions. When a RFID tag comes within the range of the reader, the tag is activated and starts sending data. The reader captures these data, decodes them, and sends them back over a wired or wireless network to a host computer for further processing.
Figure 7-18
 |
FIGURE 7-18 HOW RFID WORKS RFID uses low-powered radio transmitters to read data stored in a tag at distances ranging from 1 inch to 100 feet. The reader captures the data from the tag and sends them over a network to a host computer for processing. |
RFID systems operate in a number of unlicensed frequency bands worldwide.
- Low frequency systems (30 kilohertz to 500 kilohertz) have short reading ranges (inches to a few feet) and lower system costs. Low-frequency systems are often used in security, asset tracking, or animal identification applications.
- High-frequency RFID systems (850 MHz to 950 MHz and 2.4 GHz to 2.5 GHz) offer reading ranges that can extend beyond 90 feet and have high reading speeds. High-frequency RFID applications include railroad car tracking or automated toll collection for highways or bridges.
In inventory control and supply chain management, RFID systems capture and manage more detailed information about items in warehouses or in production than bar coding systems.
Wireless sensor networks (WSNs) are networks of hundreds or thousands of interconnected wireless devices, or nodes, that are embedded into the physical environment to provide measurements of many points over large spaces. They are based on devices with built-in processing, storage, and radio frequency sensors and antennas. The devices are linked into an interconnected network where data are routed seamlessly among all the nodes and forwarded to a computer for analysis. Wireless sensor networks are valuable in areas such as monitoring environmental changes, monitoring traffic or military activity, protecting property, efficiently operating and managing machinery and vehicles, establishing security perimeters, monitoring supply chain management, or detecting chemical, biological, or radiological material.
Figure 7-19
Wireless sensor networks (WSNs) are networks of hundreds or thousands of interconnected wireless devices, or nodes, that are embedded into the physical environment to provide measurements of many points over large spaces. They are based on devices with built-in processing, storage, and radio frequency sensors and antennas. The devices are linked into an interconnected network where data are routed seamlessly among all the nodes and forwarded to a computer for analysis. Wireless sensor networks are valuable in areas such as monitoring environmental changes, monitoring traffic or military activity, protecting property, efficiently operating and managing machinery and vehicles, establishing security perimeters, monitoring supply chain management, or detecting chemical, biological, or radiological material.
Figure 7-19
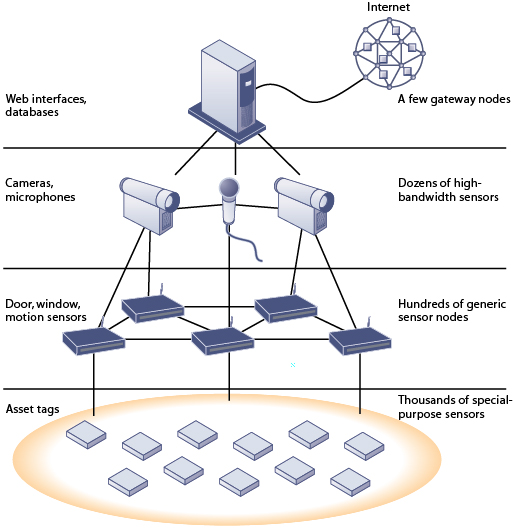 |
FIGURE 7-19 A WIRELESS SENSOR NETWORK FOR A SECURITY SYSTEM Each level of this wireless sensor network handles different types of sensing. Lower-level sensors for monitoring events, such as doors opening and closing, motion, and breakage of windows and doors, are complemented by a small group of more advanced sensors placed in key locations, such as cameras and acoustic and chemical detectors. Source: From Jason Hill, Mike Horton, Ralph Kling, and Lakshman Krishamurthy, “The Platforms Enabling Wireless Sensor Networks,” Communications of the ACM 47, no. 6 (June 2004). |


Comments
Post a Comment